TL;DR — What’s in This Issue
- 2026 momentum is real. CCC kicks off the year with new leadership for the Regulators & Standards SIG, expanding member activity, and a clear shift from awareness to real-world confidential computing deployments.
- Stronger outreach, sharper storytelling. The Outreach Committee aligns on a more strategic, full-stack approach to technical thought leadership, events, and member-driven content for 2026.
- More practical technical guidance ahead. The TAC is focused on delivering adoption-focused technical guidance and kicked off the year with a deep dive on browser-based remote attestation.
- Industry validation continues. New NVIDIA coverage underscores accelerating confidential computing adoption across CPUs, GPUs, and interconnects, matching what CCC research is already showing.
- Get involved. Upcoming events, open blog submissions, a growing job board, and multiple ways for members to contribute and amplify CCC work.
From the Executive Director
Hello Community Member,
Welcome to the New Year (that’s if you follow the Gregorian calendar, of course). I can’t remember a more busy January for the Confidential Computing Consortium. We already have three articles on our blog – do have a look. We’ve also elected a Chair (Solomon Cates, Google Cloud) and Vice Chair (Michael Guzman, JPMC) to our newly-created Regulators and Standards Special Interest Group. I’m hearing from multiple members that they expect this year to be an important and busy one around Confidential Computing, and we want to ensure that the Consortium is the place for everyone to learn about, grow and improve the ecosystem. Our Outreach and Technical Advisory Committee have new initiatives as we move from a phase of people discovering Confidential Computing to planning and rolling out deployments.
You’ll read in the article Protecting Agentic AI Workloads with Confidential Computing how important Confidential Computing is for Agentic AI, and you can expect more articles around both technical issues related to CC and applicability to particular use cases and sectors. If you’re a member of the CCC, we welcome articles, particularly around use cases or technical issues: please contact the Outreach Committee, who manage our blog and content schedules.
On a final note, the New Year is a time when lots of people are looking for new roles, and we have a job board of Confidential Computing related jobs. Again, if you’re a member, you (or your HR department!) can post roles there for free. This benefits the entire ecosystem, giving you a chance to expose interesting roles within your company while acting as a single aggregation point for job seekers.
Outreach
The Outreach Committee began 2026 by aligning on a more integrated and strategic approach to marketing and member engagement, led by the new Outreach Chair Laura Martinez and Vice Chair Rachel Wan, together with active participation from committee members. The committee is prioritizing full-stack Confidential Computing, and Secure and Sovereign AI awareness through sharing our expertise across the engagement spectrum. Specific focus will be around technical thought leadership, coordinated storytelling across tied to strategic events, and stronger activation of content brought in from member expertise. Technical blogs continue to be the highest-performing channel, and work is underway to develop a structured 2026 content calendar spanning blogs, newsletters, and event amplification.
Key updates this month include early planning for annual Outreach OKRs with mid-year reviews, progress on a unified outreach and events calendar, and continued promotion of the IDC white paper as a core thought-leadership asset.
Looking ahead, the Outreach Committee will deepen coordination with other CCC committees to surface technical content earlier, expand member participation in blogs and newsletters, and align outreach efforts with major industry milestones. Members are encouraged to submit technical blog ideas, company updates, job postings, and event announcements, and to continue amplifying CCC content across their networks.
Outreach Resources:
- Post on CCC Jobs Board:
- Subscribe to CCC Monthly Newsletter and submit content via content submission form.
- Read CCC Blog Posts: submit your blog post ideas via content submission form
- Use the Member Badge and link to the CCC Website.
- Follow the CCC Events Calendar.
Upcoming Events:
- OC3, March 12, 2026 (Hybrid: Online + Berlin)
From the TAC
The TAC is kicking off 2026 focusing on a mission from the Board to deliver more technical guidance docs to help people adopt Confidential Computing. If you’d like to help shape the document, join us at one of our meetings on alternating Thursdays at 7 am pacific time. You can look up the meeting in your own timezone using the CCC Calendar.
We also had our first TAC Tech Talk of the year. Rüdiger Kapitza and Luca Preibsch gave a detailed presentation on the topic “Browser-based Remote Attestation”.They also discussed their follow-up work on runtime attestation and the possibility of using site certificates for attestation. You can watch this and previous talks on our Tech Talk Playlist.
Recent News
- CCC Outlook for 2026: A Message from Executive Director Mike Bursell
- Mike Bursell, Executive Director of the Confidential Computing Consortium, shares the CCC’s outlook for the year ahead and why momentum is accelerating across the ecosystem.
- From growing regulator interest and AI security needs, to digital sovereignty, attestation, and a clear shift toward demand-side adoption, this post outlines where Confidential Computing is heading and how the CCC is focusing its work in 2026.
- CCC Executive Director Mike Bursell Named to OpenUK New Year Honours List 2026
- Congratulations to Mike Bursell, Executive Director of the Confidential Computing Consortium, on being named to the OpenUK New Year Honours List for 2026.This recognition celebrates his long-standing contributions to open source and his leadership in advancing confidential computing as a foundation for security, privacy, and trustworthy systems. Read the announcement.
- Protecting Agentic AI Workloads with Confidential Computing
- As AI systems become more autonomous, protecting agent identity and data becomes critical. This new blog from Mike Bursell explores a growing gap in AI security: Agentic AI systems can be tampered with unless their identity, workloads, and data are protected. It explains how Confidential Computing provides hardware-based isolation and attestation to help make autonomous agents more trustworthy and verifiable. Read the blog.
- Nvidia Touts New Storage Platform, Confidential Computing For Vera Rubin NVL72 Server Rack
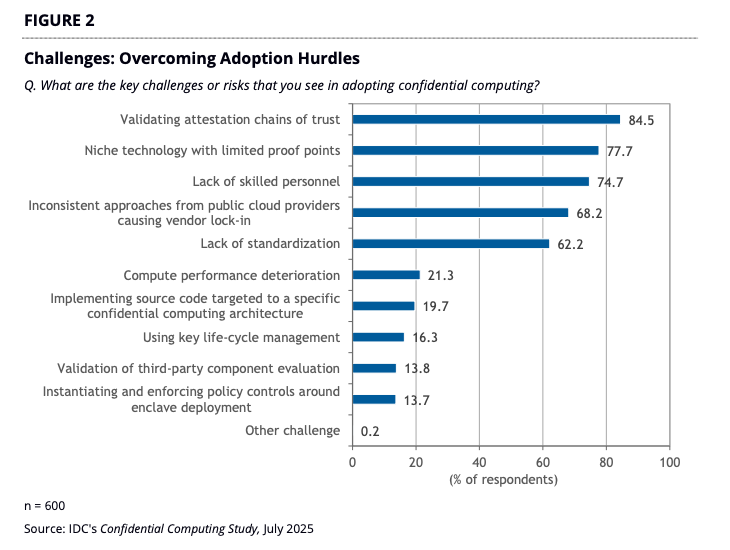
- New coverage on NVIDIA’s Rubin NVL72 highlights a major shift: confidential computing is extending across CPU, GPU, and interconnects, enabling organizations to verify trust cryptographically rather than rely on contractual assurances. This momentum reflects what our ecosystem is already seeing. CCC and IDC research shows that 75% of organizations are adopting confidential computing, with production deployments accelerating across regulated and high-risk environments.